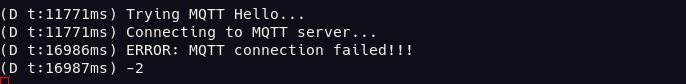
Hi @bedinek ,
Thanks for the suggestion!
Please note that the RPi is running Pi-hole and also managing DHCP - this may have an impact on the outputs below.
My SCK2.1 responds to the mqttsrv command with:
Mqtt Host: 192.168.2.101
Mqtt Port: 1883
So I can monitor incoming connections on port 1883 on the RPi (192.168.2.101) using:
sudo tcpdump dst port 1883
Nothing appears in the tcpdump from the SCK2.1 however.
Testing a mqtt publishing python script (as described above earlier) from my Ubuntu machine (192.168.2.226) does appear in the tcpdump output however:
21:47:51.315252 IP 192.168.2.226.47815 > 192.168.2.101.1883: Flags [S], seq 1355256520, win 64240, options [mss 1460,sackOK,TS val 3881306389 ecr 0,nop,wscale 7], length 0
21:47:51.315344 IP 192.168.2.101.1883 > 192.168.2.226.47815: Flags [S.], seq 4225788666, ack 1355256521, win 65160, options [mss 1460,sackOK,TS val 822255602 ecr 3881306389,nop,wscale 7], length 0
21:47:51.316405 IP 192.168.2.226.47815 > 192.168.2.101.1883: Flags [.], ack 1, win 502, options [nop,nop,TS val 3881306390 ecr 822255602], length 0
21:47:51.316497 IP 192.168.2.226.47815 > 192.168.2.101.1883: Flags [P.], seq 1:15, ack 1, win 502, options [nop,nop,TS val 3881306390 ecr 822255602], length 14
21:47:51.316536 IP 192.168.2.101.1883 > 192.168.2.226.47815: Flags [.], ack 15, win 509, options [nop,nop,TS val 822255603 ecr 3881306390], length 0
21:47:51.316582 IP 192.168.2.226.47815 > 192.168.2.101.1883: Flags [FP.], seq 15:58, ack 1, win 502, options [nop,nop,TS val 3881306390 ecr 822255602], length 43
21:47:51.317100 IP 192.168.2.101.1883 > 192.168.2.226.47815: Flags [P.], seq 1:5, ack 59, win 509, options [nop,nop,TS val 822255604 ecr 3881306390], length 4
In the SHELL, while testing, I’ve turned on debug -esp and get messages such as:
Sending msg to ESP with 3 parts and 165 bytes
{t:2021-08-22T19:21:30Z,10:99,14:12,55:22.43,56:69.52,53:27.28,58:100.37,113:21.00,112:541.00,128:0,125:49.759043,126:6.637683,127:34.85,129:0.00,131:9999.00,130:0}
Sent part num 0
{t:2021-08-22T19:21:30Z,10:99,14:12,55:22.43,56:69.52,53:2
Sent part num 1
7.28,58:100.37,113:21.00,112:541.00,128:0,125:49.759043,126
Sent part num 2
:6.637683,127:34.85,129:0.00,131:9999.00,130:0}:EA:A0","es
Receiving msg from ESP in 1 parts
Network publish OK!! (15 readings)
I’ve also tried while debug is off as I’d read somewhere in the code it can cause problems with communication.
By looking at the Pi-hole DHCP table I can see that 192.168.2.219 is the IP of the SCK2.1.
Is there an easier way to retrieve the IP of the SCK2.1 in the SHELL?
I’ve also tried monitoring using the following command:
sudo tcpdump host 192.168.2.219 -vv
And received this:
21:50:24.737780 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.2.101 is-at dc:a6:32:c4:71:f6 (oui Unknown), length 28
21:50:24.742115 IP (tos 0x0, ttl 255, id 3, offset 0, flags [none], proto UDP (17), length 66)
192.168.2.219.43050 > 192.168.2.101.domain: [udp sum ok] 25898+ A? mqtt.smartcitizen.me. (38)
21:50:24.742635 IP (tos 0x0, ttl 64, id 61650, offset 0, flags [DF], proto UDP (17), length 82)
192.168.2.101.domain > 192.168.2.219.43050: [udp sum ok] 25898 q: A? mqtt.smartcitizen.me. 1/0/0 mqtt.smartcitizen.me. A 85.159.210.156 (54)
21:50:24.742942 IP (tos 0x0, ttl 255, id 4, offset 0, flags [none], proto UDP (17), length 66)
192.168.2.219.43050 > 192.168.2.101.domain: [udp sum ok] 25898+ A? mqtt.smartcitizen.me. (38)
21:50:24.743302 IP (tos 0x0, ttl 64, id 61651, offset 0, flags [DF], proto UDP (17), length 82)
192.168.2.101.domain > 192.168.2.219.43050: [udp sum ok] 25898 q: A? mqtt.smartcitizen.me. 1/0/0 mqtt.smartcitizen.me. A 85.159.210.156 (54)
21:50:24.746092 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.1 tell 192.168.2.219, length 50
21:50:24.746524 IP (tos 0x0, ttl 255, id 6, offset 0, flags [none], proto ICMP (1), length 56)
192.168.2.219 > 192.168.2.101: ICMP 192.168.2.219 udp port 43050 unreachable, length 36
IP (tos 0x0, ttl 64, id 61651, offset 0, flags [DF], proto UDP (17), length 82)
192.168.2.101.domain > 192.168.2.219.43050: [|domain]
21:50:28.807849 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.2.219 tell 192.168.2.101, length 28
I’m not very clear on what’s happening here but the fact that mqtt.smartcitizen.me is appearing suggests to me that either it’s checking with the pi-hole whether this host is on the black list and/or it’s trying to communicate with that host.
This suggests that the mqtt hostname hasn’t been overwritten, no?
I have a second SCK2.1 running stock firmware. It produces a similar tcpdump output (from another IP).
What are your thoughts on this?